The Exploit Database - Exploits, Shellcode, 0days, Remote Exploits, Local Exploits, Web Apps, Vulnerability Reports, Security Articles, Tutorials and more.
Scan your WordPress website below to get free & instant access to your ... I declare that I have permission to scan this domain and that I agree with the Terms of Use. ... Remarkably enough thousands of WP sites are vulnerable to attacks and get hacked each day. ... Source: The Hacker News, March 2014 (view full article) .... Ethical Hacking and Penetration Testing Made Easy Patrick Engebretson. Notice that both scanning and spidering are available in this “Attack” menu. ... of web scanning to understand: the scanner is not trying to exploit the website, but rather .... Every chapter will have foundational knowledge so that you know the why of the ... of Web Hacking provides an overview of current web vulnerabilities and how our ... to exploit other web users by exploiting web application cross-site scripting .... Creating a full-featured dynamic website involves data manipulation, user ... In this article we'll go about a short definition of what is hacking, how it's done in web ... Recognition phase — Know your target; Cross-site-scripting — XSS; Cross ... is undoubtedly the consequence of exploiting various vulnerabilities on a server.. Ethical hacker shares website hacking techniques your WordPress site ... Here's a reality check for you from someone who does ethical hacking for a ... that have common vulnerabilities in them that can be easily exploited.
Statistics show us that SQL Injection and XSS vulnerabilities are still the most dangerous threats. ... and use web application security scanners to scan and secure their websites. ... After analysing statistics of web application hacking attacks happening all ... security risks, i.e. the most commonly exploited web vulnerabilities.. Most websites store valuable information such as credit card numbers, email address and passwords etc. How you can protect web servers from hackers. ... is an open source tool for developing, testing and using exploit code. It can be used to discover vulnerabilities in web servers and write exploits that .... SQL Injection attack is the most common website hacking technique. ... of websites, testing many types of injection attacks until they are successful. ... Cross Site Scripting is a major vulnerability that is often exploited by .... Here's our updated list of 15 sites to practice your hacking skills so you can be the ... Alright, this one isn't exactly a vulnerable web app – but it's another engaging way of ... The game is designed to test your AppSec skills and each question offers a ... exploit web applications; Learn how hackers find security vulnerabilities ...
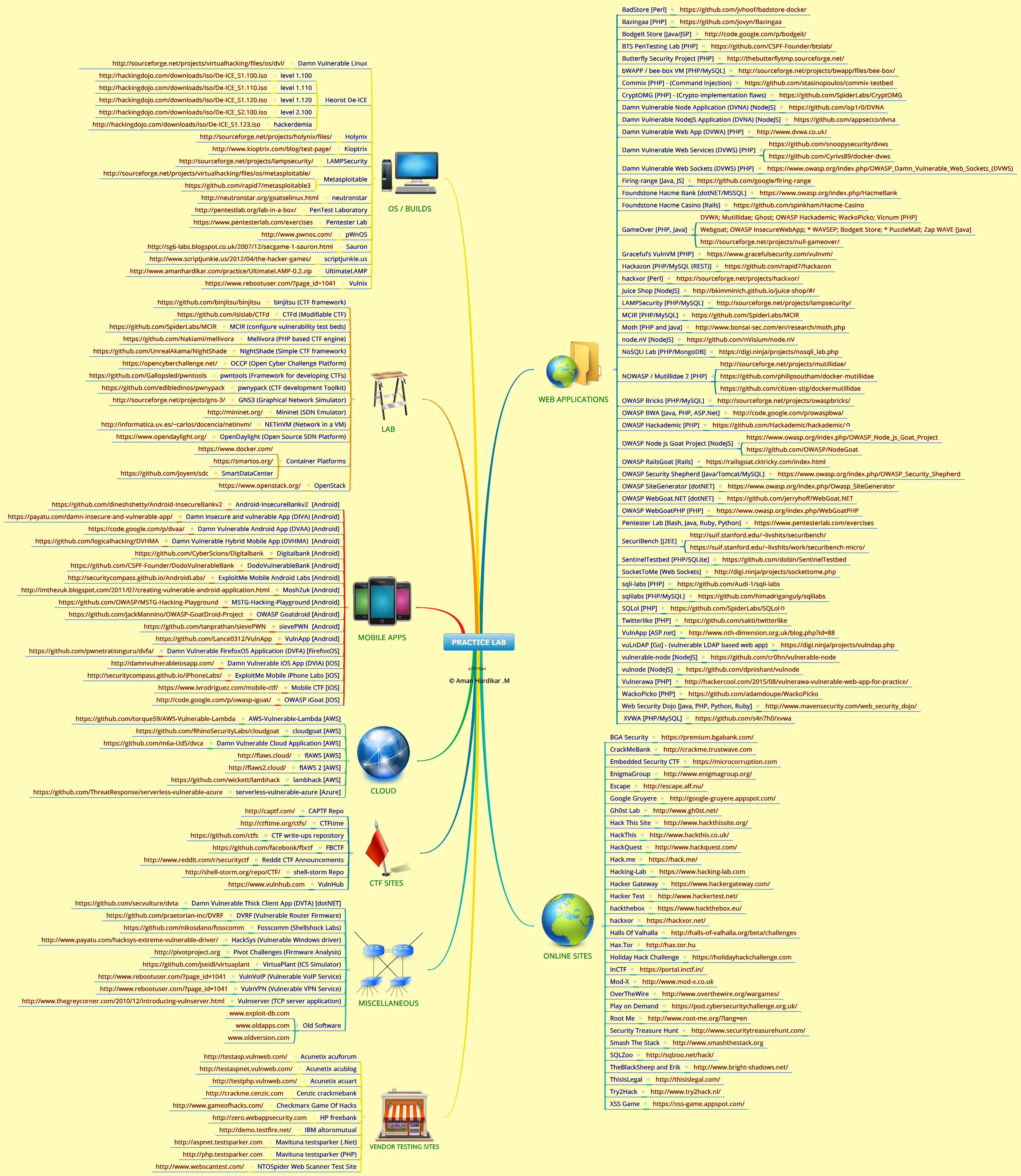


Man-in-the-middle attack one of a class of hacks where the attacker eavesdrops on ... The test exposed a lot of security loopholes in the Web site. ... When the user visits these hacked Web sites, malicious JavaScript exploits vulnerabilities in .... For organizations that found vulnerabilities before they were exploited using HackerOne, ... Improve your Pen Test results with a project-based vulnerability assessment program ... program that consistently outperforms traditional penetration testing. ... Peter Yaworski is the author of Web Hacking 101, is a full-time appsec .... Good Web vulnerability scanners and tools can help ensure that you get the most from ... tools in my work testing Web sites and applications for vulnerabilities. ... as exploit tools, such as Metasploit, when testing Web servers and applications.. There are many ways to learn ethical hacking and pen testing, whether it's ... There are fun, game-oriented platforms here, with both web and mobile ... They also encourage people to exploit this site literally, and reward those .... Learn how hackers exploit web applications! ... The best way to learn things is by doing, so you'll get a chance to do some real penetration testing, actually exploiting a ... web security vulnerabilities, like cross-site scripting vulnerabilities (XSS) and ... In this codelab, you'll use both black-box hacking and white-box hacking. eff9728655